© 2024 Sudotouch LLC. All rights reserved.
Secure technology should drive progress, not slow it down. SudoTouch creates software that is built to help government and industrial teams move faster, reduce extra duty workload, strengthen compliance, and deliver results with confidence.
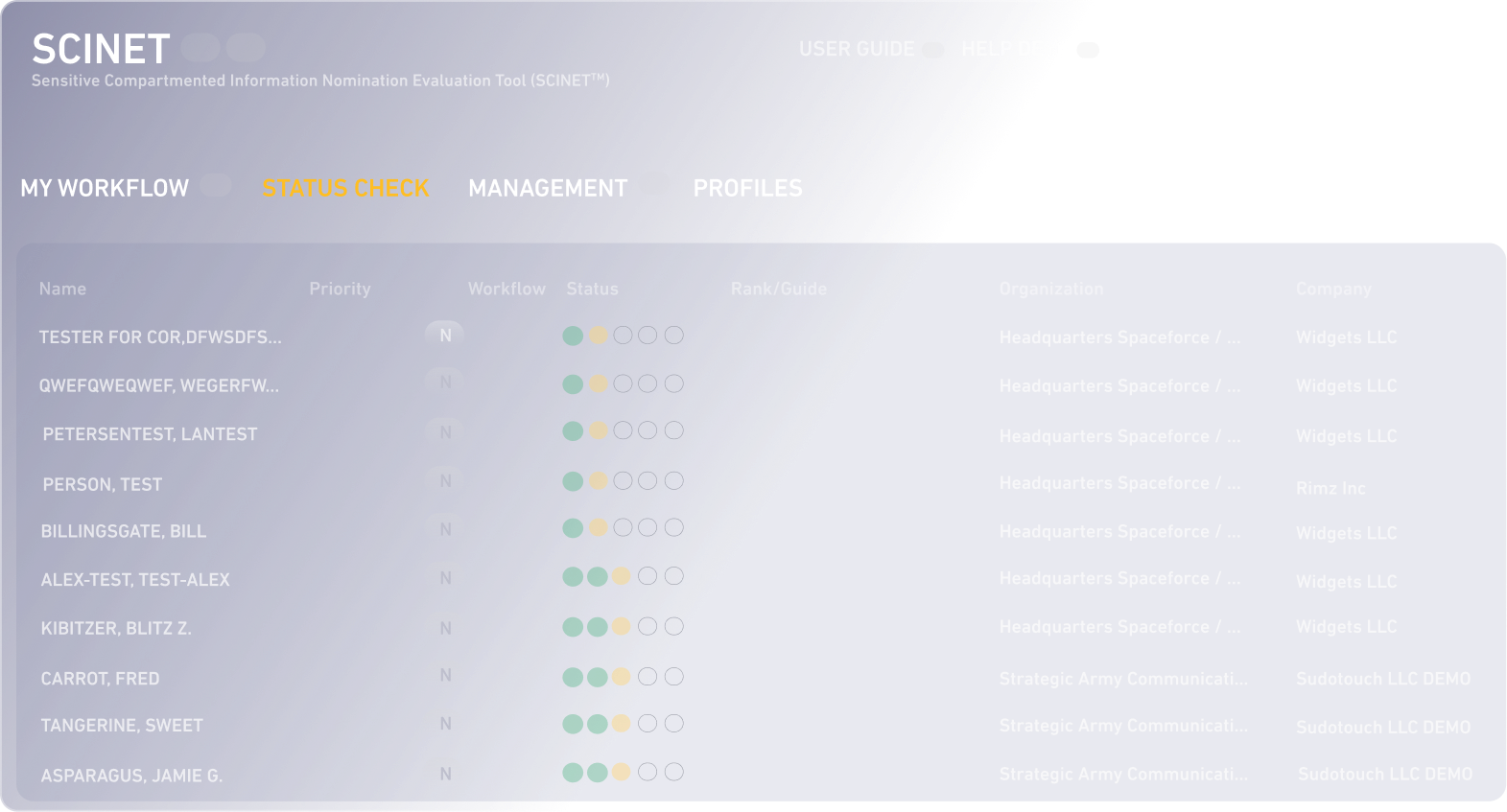
SCINET is government-purpose software that streamlines SCI access management by automating the full lifecycle, from nomination through debrief, while ensuring compliance with DoDM 5105.21 and NISPOM requirements.
It enables cognizant security professionals to:
• Reduce processing time by 65%
• Eliminate manual errors and lost paperwork
• Gain real-time visibility into nomination status
• Automate compliance with full control of transmitted CUI

SCINET for Industry is built on the same proven architecture utilized by the government SSO, adapted for contract security program management. security program management, and powered by SudoTouch's proprietary technology, CAIS and WAIS.
It offers Contractor Special Security Officers:
• Turnkey NISPOM and DoDM compliance for SCI access nomination requirements
• Exportable professional access nomination packages
• Full digital compatibility with SCINET for Government
• Secure nominee interface for internal communication of CUI