© 2024 Sudotouch LLC. All rights reserved.

We deliver solutions to the administrative burden of government and industrial security management.
Is managing access to SCI, processing requests for system/area accesses, or managing SCIFs involving a mix of ad-hoc tracking mechanisms and communication methods?
The solution is here
Our PKI-enabled secure applications perform and automate these processes, reduce administrative workload up to 70%, secure communications, and ensure compliance with all regulations.

Is your company juggling CUI for access request packages across unsecure platforms like messaging apps, email, or cloud-based folders?
We can help
Our seamless applications consolidate internal/external communication chains between government and industry partners, eliminating vulnerability from email, messaging apps, and other ad-hoc methods.

SudoTouch designs, develops, and deploys software applications that produce the official functions required for access management to SCI/SAP and other controlled areas, information, and systems for both government and industry.

The SudoTouch proprietary:
Important tasks no longer perish in the soup of email workflows, and consensus is easily reached on contract attributes such as:


Your Challenges: Manually managing SCI access is time-consuming and error prone. Ad-hoc tracking mechanisms and manual workflows are inconsistent and sometimes confusing for the industrial security managers and new government personnel.
Our Solution: SCINET automates the entire lifecycle of SCI access management, from nomination to debrief, while ensuring compliance with DoDM 5105.21 and NISPOM requirements. New personnel find the system intuitive and are easily onboarded into a fully-compliant operation.
The Impact:

Your Challenges: Manually managing SCI or SAP access nomination packages and company compliance is time-consuming, error-prone, and filled with security vulnerabilities for CUI through ad-hoc communication channels.
Our Solution: SCINET for Industry empowers the Facility Security Officer and nominated employees with an intuitive interface to build and submit packages to the government, manage SETA training, and securely communicate internally.
The Impact:
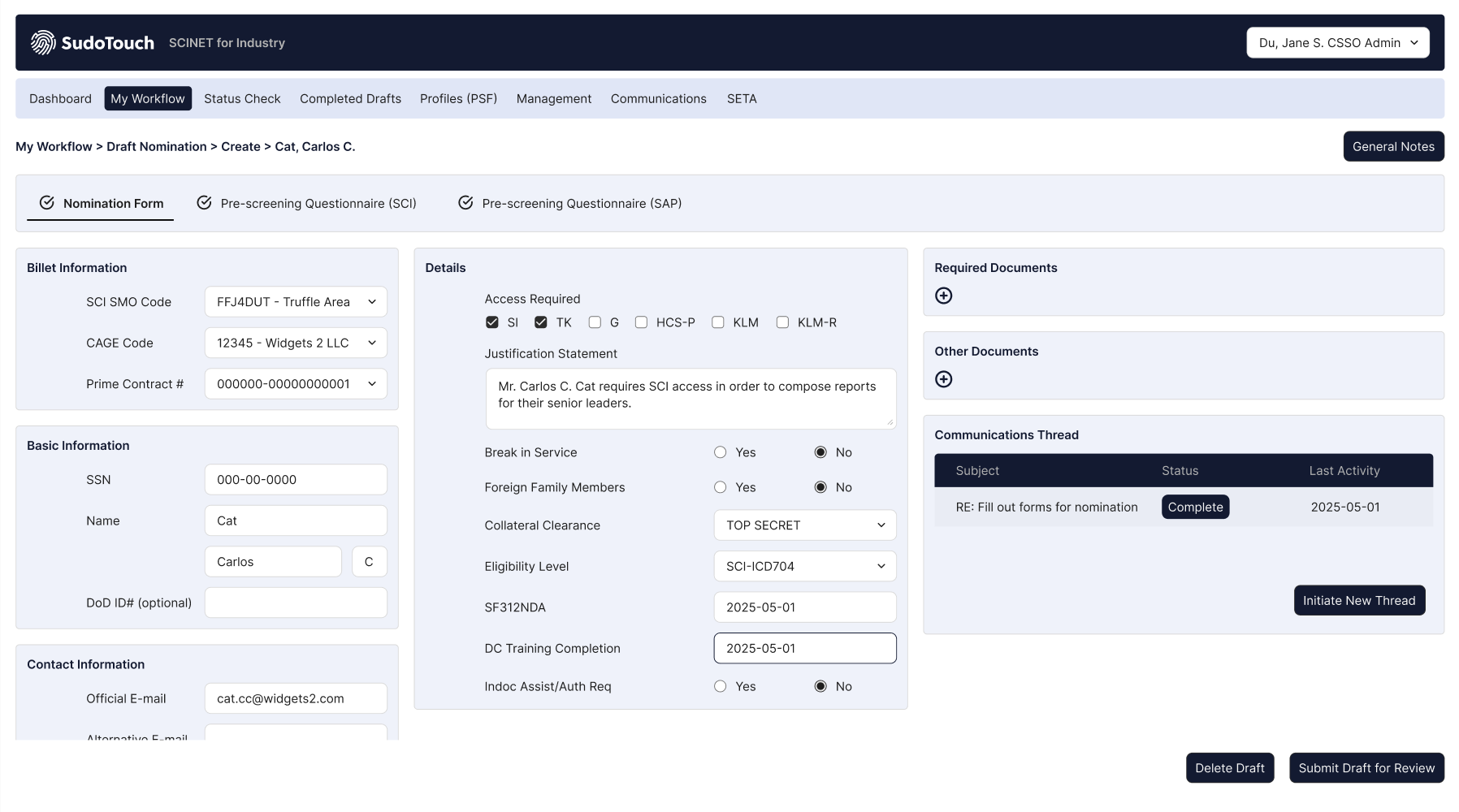
Your Challenges: Meeting DoDM 5105.21,NISPOM, and SAP nomination requirements while managing groups of non-conventional employees in unique environments (e.g. research institutions, unique partnerships, etc.).
Our Solution: SCINET Starter empowers the security manager and nominated employees with an intuitive interface to build and submit packages to other government entities, manage SETA training, and securely communicate internally with nominees.
The Impact:

Your Challenges: The SCIF buildout process, accreditation, management, and decommissioning involves complex regulatory requirements. It is decentralized and confusing.
Our Solution: SCIF Cred provides end-to-end management of the SCIF lifecycle, from accreditation to decommissioning. Protected via PKI at the unclassified level, instances are also deployable to classified level environments.
The Impact:

Your Challenges: Controlling physical access to sensitive areas creates administrative overhead. It must be tracked and monitored with 100% accountability of all issued credentials.
Our Solution: RAANET simplifies the management of controlled/restricted area access, and fully emulates all the requirements of the AF IMT 2586 with an intuitive interface.
The Impact:

Your Challenges: Manual management of system access requests creates excessive workload, bottlenecks, and security risks. The DD Form 2875 (SAAR) confuses applicants with ambiguous fields.
Our Solution: SANET streamlines workflows for system access requests, automatically vets the applicant against contract data, and organizes the official records congruent with regulations.
The Impact:

Our team of military veterans and software developers has walked in your shoes. We understand the challenges you face because we've faced them too.

Our solutions are already parked in DoD systems.

Our clients report: 60-70% reduction in administrative workload, enhanced security posture, improved cross-domain communication, streamlined compliance with DoD regulations

All SudoTouch applications are built to function in full compliance with the governing regulations. This means that applications are built around how customers operate in the real world.

SudoTouch posts directly in the Platform One Solutions Marketplace and the Tradewinds Solutions Marketplace to enable the utilization of a variety of contract vehicles, and is considered “competed” for award purposes. Additionally, our solutions contain Small Business Innovation and Research (SBIR) technology, which is eligible for direct award of a Phase III contract vehicle.
Our applications are built with the collaboration of trusted partners utilizing DevSecOps practices. We share our partners’ commitment to excellence and leverage innovation to provide secure solutions to complex administrative problems.





SudoTouch offers a wide range of customization services designed to meet the unique needs of each customer’s regulatory requirements and user base. We want to help you implement effective solutions that are readily adopted by your team.